For years, insurance industry pundits predicted that cyber-related losses could lead to directors’ and officers’ liability. Prior to 2017, that concern was largely overstated since most headlining cyber breaches resulted in dismissal of the related ‘follow on’ shareholder derivative directors’ and officers’ (D&O) litigation.
However, 2017 is a different story. The $350million Yahoo! purchase price reduction following its disclosure of massive breaches, the WannaCry ransomware incident, the NotPetya ransomware incident and the Equifax security breach have changed the paradigm. How do we know?
“PRIOR TO SUFFERING A CYBER INCIDENT, BUSINESSES SHOULD CONFER WITH KNOWLEDGEABLE COUNSEL AND TECHNOLOGY CONSULTANTS TO IMPLEMENT CYBERSECURITY MEASURES AND COMPLIANCE PROCEDURES”
1. Increased public company disclosures of cyber incidents that have a material impact on the organisations’ financial statements
2. Increased public company disclosures of potential material cyber risks[1]
3. Increased regulatory scrutiny[2]
4. Resignations of public company officers
5. The $5billion drop in Equifax market capitalisation
Cyber events now rank among the top three triggers for D&O derivative actions (along with M&A activity and environmental issues).
What are a board’s duties with respect to cyber risk management and disclosure?
On 13 October 2011, the US Securities and Exchange Commission’s (SEC) Division of Corporation Finance issued a non-binding guidance on reporting obligations for public companies regarding cybersecurity risks and cyber incidents (the Disclosure Guidance). The Disclosure Guidance recognised that the growing reliance of companies on digital technologies meant that such risks and events could be sufficiently material to investors that they may be required to be disclosed in public securities filings.
How much information is vital to investors depends a lot on who is defining what information is material and what is immaterial. Generally, according to the SEC, information is material if it ‘limits the information required to those matters to which there is a substantial likelihood that a reasonable investor would attach importance in determining whether to purchase the security registered’.
In the US, directors are held to standards of fiduciary duty, loyalty and care, with the business judgement rule as a defence against many allegations of wrongdoing. The ability to demonstrate that directors have appropriately discharged their duties often dictates the ability to successfully rebut claims made against such individuals. Outside of the US, the standard to which corporate leaders are held in many cases is higher. For example, the European Union General Data Protection Regulation (GDPR) intends to strengthen and unify data protection for all individuals within the European Union, with potential penalties of up to four per cent of an organisation’s worldwide revenues for noncompliance. All of these factors lead to significant care required of directors and officers and ensure that appropriate cyber controls are in place. It is interesting to examine recent cyber incidents and the frequency of follow-on D&O litigation in the US.
Selected cyber breaches
A brief scan of notable cyber breaches[3] in the public record includes the table (below).

Most of these matters have been dismissed with corporate defendants successfully rebutting the alleged wrongdoings. There are some lessons to be learned with regard to appropriate planning to reduce cyber risk and the successful defences asserted by corporate boards. One such example comes from the Wyndham cyber breach. In brief, a shareholder derivative suit was filed against Wyndham and its directors and officers in 2014. The suit alleged that Wyndham failed to implement adequate cybersecurity measures and disclose the data breaches in a timely manner, which caused the company to suffer damages. Ultimately, the court disagreed with the plaintiffs, citing that Wyndham and its directors and officers utilised appropriate (un-conflicted) counsel, the board investigated and took reasonable steps to familiarise itself with the allegations of the derivative demand, the board had taken prudent steps to familiarise itself with cyberattacks and had discussed the attacks at multiple board and committee meetings.
The Wyndham litigation provides several important lessons for businesses that may be subject to a cyber risk incident:[4]
1. Prior to suffering a cyber incident, businesses should confer with knowledgeable counsel and technology consultants to implement cybersecurity measures and compliance procedures. The board should document the steps taken to evaluate a company’s cyber exposures, the resulting recommendation, and, most importantly, the actions completed as a result
2. Following a cyber incident, businesses must be prepared to respond to civil legal proceedings and government regulatory inquiries and investigations. The best protection from such challenges is having a documented deliberative process resulting in formal prevention and crisis response plans that were routinely monitored
Impact to business results and financial reporting
In most situations where personally identifiable information (PII) was a prime source of the alleged breach, there was generally limited actual damage to the value of the business at hand. As of 31 December 2016:
- 85 per cent < $1million damages
- 10 per cent between $1million to $20million damages
- 5 per cent > $20million damages
While PII will continue to be a prime source of cybersecurity exposure, it is expected that business interruption (i.e. supply chain), bodily injury (i.e. transportation GPS), tangible property damage (i.e. manufacturing hack and Internet of Things) and actual diminution in financial results (and, therefore, business valuation) will increasingly arise from cyber exposures. According to the 2017 Ponemon Global Cyber Risk Transfer Comparison Report:[5]
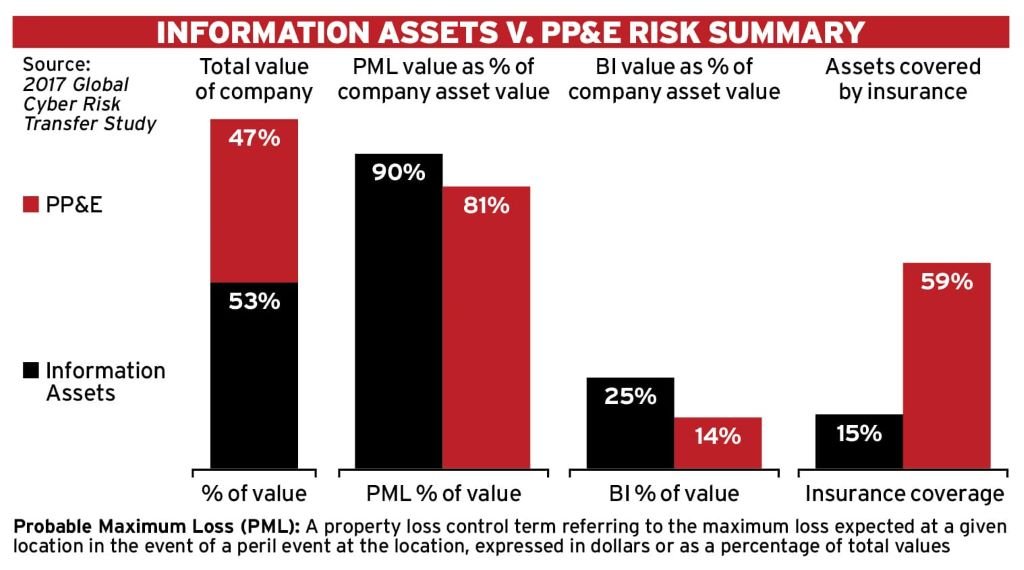
- The impact of business disruption to cyber assets is 72 per cent greater than to property, plant and equipment (PP&E) assets
- Quantification of probable maximum loss from cyber assets is 27 per cent higher than from PP&E
- Organisations valued cyber assets 14 per cent more than PP&E assets
- Organisations insure on average 59 per cent of PP&E losses, compared to an average of 15 per cent of cyber exposures
Growing impact of cyber assets and exposures
Yahoo! The Yahoo! cyber breach, in which more than three billion user accounts were impacted, led to a material impact to deal valuation and significant repercussions for Yahoo! leadership:
- Verizon Communications Inc. acquired Yahoo! Inc.’s internet properties at a $350million discount after revelations of security breaches
- Yahoo! general counsel Ronald Bell has left the company after an investigation of security breaches
- It was found that the legal team had enough information to warrant further inquiry but didn’t sufficiently pursue it[6]
- Yahoo! chief executive officer, Marissa Mayer, has foregone her annual bonus, due to the breach
NotPetya In June 2017, A.P. Moller-Maersk,[7] Mondelez,[8] Reckitt Benckiser,[9] Merck,[10] DLA Piper Law Firm[11] and DT Express, a FedEx subsidiary based in the Netherlands,[12] among other organisations, announced that the NotPetya virus had crippled supply chain operations.
The malware, disguised to appear as a ransomware attack, wiped the computers’ data instead. FedEx Corp. estimates it took a $300million hit from the late June cyberattack that started by targeting Ukrainian companies and spread globally, particularly affecting FedEx subsidiary TNT Express.
The attack resulted in a significant business interruption and financial impact. According to FedEx CFO Alan Graf: “The impact from lost revenues was and continues to be more heavily weighted toward our higher-yielding international shipments, resulting in a more pronounced impact on profits. It is taking longer to restore our international business due to the complexity of clearance systems and business processes.” Unfortunately, as FedEx explained to investors, the company did not have a cyber policy in place that would cover this type of attack.
Equifax13 Equifax announced that its CEO, Richard Smith, had retired following similar retirements by its top information security executives, the chief information officer and chief security officer. The market has continued to punish Equifax shareholders. The company’s market capitalisation was down nearly 30 per cent or about $5billion. As of 21 September 2017, more than 100 lawsuits had been filed, including shareholder derivative litigation against the directors and officers, some of whom sold stock between the 29 July 2017 date of discovery of the breach and the 7 September 2017 public disclosure of the incident.
Each of these instances – Yahoo!, NotPetya and Equifax – are examples of the evolving business impact resulting from cybersecurity breaches and the financial reporting considerations that follow. In each of these recent incidents, companies either had to disclose the materiality of the cyber breach as it relates to their financial reporting, or publicly reference the impact to future earnings and business operations resulting from the breach
“THE BRAVE NEW WORLD OF CYBERSECURITY AND THE NEED FOR BOARD-LEVEL FOCUS ON RISK ASSESSMENT, QUANTIFICATION, TESTING, MITIGATION, TRANSFER AND RESPONSE, DEMANDS THAT CORPORATE LEADERSHIP CANNOT BE COMPLACENT”
Going forward: be proactive

The brave new world of cybersecurity and the need for board-level focus on risk assessment, quantification, testing, mitigation, transfer and response, demands that corporate leadership cannot be complacent (see AON Framework, right). A number of realities have emerged from recent cyber incidents that corporate leaders should consider, including the following:[14]
1. Cybersecurity presents equal, if not more, risk than financial reporting failure and should receive the same level of oversight and audit
Organisations formulating their cybersecurity oversight need look no further than the current chief financial officer oversight paradigm for financial accounting and reporting. Organisations should establish governance procedures to oversee a corporation’s cybersecurity wellness substantially similar to those that have proven effective and sufficiently flexible to assess and validate financial statement accuracy and reliability.
2. Financial reporting related to cybersecurity is an increasing concern
While the disclosures required are a matter of regulation and statute, investors’ and regulators’ expectations about information to be disclosed evolve over time and the recent emergence of cybersecurity concerns are driving changes with regard to disclosure expectations.
3. Insurance as an effective risk reduction tool
As a general matter, D&O policies have responded effectively to cyber-related litigation. Cyber insurers are evolving with broader coverage and greater capacity to address the growing cyber threat. Property, general liability, crime (i.e. social engineering funds transfers), K&R (i.e. ransomware), EPLI and professional liability insurance programmes may also provide elements of risk transfer protection from cyber exposures.
A comprehensive cyber risk management programme can help serve to effectively achieve positive insurance programme results, aim to reduce an organisation’s cyber exposure and ultimately lead to a more resilient organisation
Conclusion
While there’s never been a more challenging time to be a director or officer given the intersection of information technology and corporate governance, there has never been a more exciting time to provide risk management advice given the growing complexity of risk. Insurance, both cyber and D&O, can be core compoPullnents of a company’s risk mitigation efforts. A well-crafted insurance programme can help maximise the recoveries available, both in efforts to remediate corporate breaches as well as to help protect the insured organisation’s and individual directors’ assets.
Footnotes:
1. A July 26, 2017 Bloomberg article entitled Corporate Cyber Security Risk Disclosures Jump Dramatically in 2017 reports that “more public companies described ‘cybersecurity’ as a risk in their financial disclosures in the first half of 2017 than in all of 2016, suggesting that board fears over data breaches may be escalating.”
2. Newly appointed SEC chair Jay Clayton has emphasised that disclosure requirements extend to cybersecurity issues, stating that “public companies have a clear obligation to disclose material information about cyber risks and cyber events. I expect them to take this requirement seriously.” (July 12, 2017), https://www.sec.gov/news/speech/remarks-economic-club-new-york).
3. Multiple SEC filings: https://www.sec.gov/edgar/searchedgar/companysearch.html
4. Bracewell, Lessons for Corporate Directors from the Wyndham Data Breach Derivative Action http://www.bracewelllaw.com/news-publications/updates/lessons-corporate-directors-wyndham-data-breach-derivative-action.
5. 2017 Ponemon Global Cyber Risk Transfer Comparison
6. Brian Womak, Yahoo! Counsel Leaves After Hack Investigation Finds Lack of Action https://www.bloomberg.com/news/articles/2017-03-01/yahoo-counsel-bell-leaves-after-hack-probe-finds-lack-of-action.
7. http://files.shareholder.com/downloads/ABEA-3GG91Y/5012608953x0x954059/3E9E6E5C-7732-4401-8AFE-F37F7104E2F7/Maersk_Interim_Report_Q2_2017.pdf; http://www.maersk.com/en/the-maersk-group/press-room/press-release-archive/2017/^8/a-p-moller-maersk-interim-report-q2-2017
8. http://files.shareholder.com/downloads/AMDA-1A8CT3/4967206879x0xS1193125-17-245459/1103982/filing.pdf
10. https://www.ft.com/content/3d7ac341-1742-3329-9a15-2dc269522d10
11. https://www.ft.com/content/1b5f863a-624c-11e7-91a7-502f7ee26895; 3 Lessons For Firms After Cyberattack on DLA Piper
12. 7/17/2017 SEC 10K Filing, pg 43 https://www.sec.gov/Archives/edgar/data/1048911/000095012317006152/fdx-10k_20170531.htm
13. Equifax Press Release, Equifax Announces Cybersecurity Incident Involving Consumer Information (Sept. 7, 2017), https://investor.equifax.com/news-and-events/news/2017/09-07-2017-213000628.
14. David R. Fontaine and John Reed Stark, Yahoo’s Warning To GCs: Your Job Description Just Expanded https://www.law360.com/privacy/articles/907583/yahoo-s-warning-to-gcs-your-job-description-just-expanded.

